Featured Courses
Scroll to Item 1
Scroll to Item 2
Scroll to Item 3
Interested in Crest + Oral-B Products?
Crest+Oral-B iO Electric Toothbrush System - Professional Personal Use
Order NowCrest+Oral-B iO Transformational Gum Health Electric Toothbrush System
Order NowCrest + Oral-B iO Ortho Essentials Electric Rechargeable System
Order NowPurchase Oral-B Electric Toothbrushes at Professional Pricing Today!
Learn MoreScroll to Item 1
Scroll to Item 2
Scroll to Item 3
Scroll to Item 4
Professional Resources
Closing America's Smile Gap
Winners AnnouncedAnnouncing the Crest + Oral-B Scholarship Programs!
Apply Today!Crest®+ Oral-B®- Helping Your Patients Transform Their Oral Health
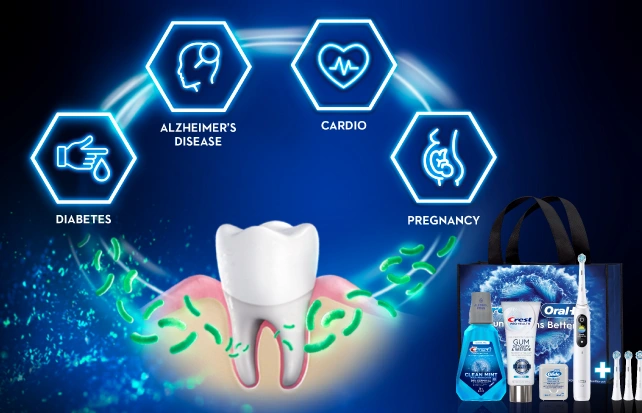
Whole Body HealthScroll to Item 1
Scroll to Item 2
Scroll to Item 3
Student & Faculty Quick Links
Enter Assignment Number
Use the Assignment Number provided to find the course
Create assignments with a wide range of courses available
Review the submitted Assignments
Case studies for students and professionals
Interactive learnings for you